Interactive Report Summary
Q4 2020 and Year in Review Threat Report
Top Findings at a Glance
Lesson learned in 2020: Cybersecurity is not a solo effort.
COVID-19 and work-from-home taught us a few things: the importance of deployment speed, the necessity of assuming new levels of risk and the necessity of working with what we have. The top takeaway? Cybersecurity has to be customized and multipronged in its strategy.

Cybersecurity advisory for healthcare organizations targeted by Trickbot and BazarLoader malware in Q4.
Hashes, domains and IP addresses for Emotet and Trickbot/BazarLoader malware.
Methodology
Hover over tiles to learn more
Q4 202O in Review
October through December
Total Events
Unique Variants
Total Activity
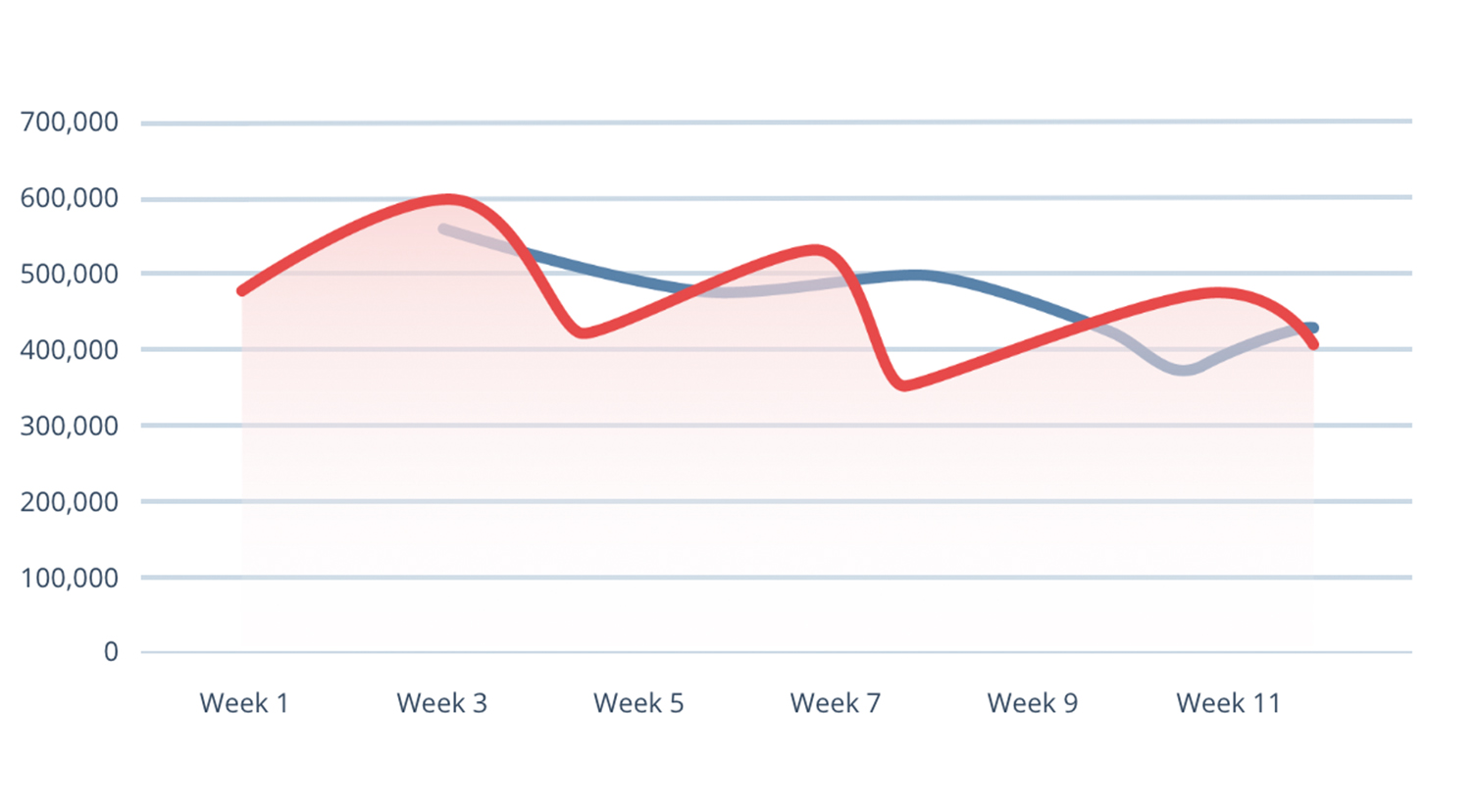
Malware
Detection, Q4 2020Total activity in Q4 declined by 30.7% but still increased by 57.93% compared to Q3.
How to Combat
To strengthen your defenses against malware activity you’ll need to adopt a multiprong approach including endpoint protection platforms and cyber awareness training.
Malware
Malware activity declined steadily throughout the first part of the year and bottomed out in July. VBA agent activity caused a 467% spike in September, but Q4 activity trailed off slightly. The predominant themes in malspam emails? COVID-19, the U.S. election, invoices, shipping/package details and legal documents.
Total Events
Unique Variants
Total Activity
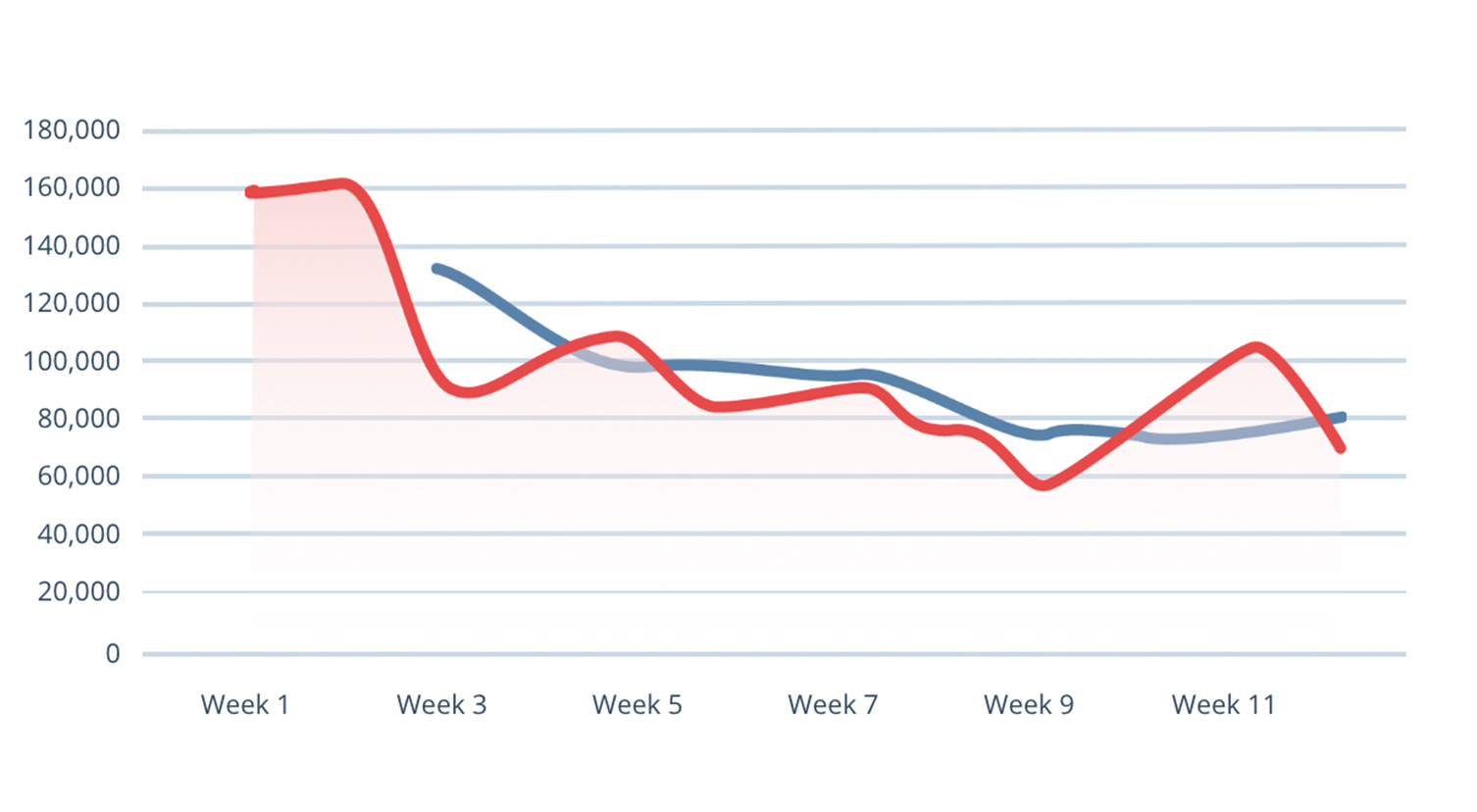
Botnets
Detection, Q4 2020Andromeda and Torpig Mebroot spiked 172% and 1,453%, respectively, although overall botnet activity declined.
How to Combat
Step up your efforts to stop botnet activity, which is usually detected post-infection. We recommend detecting malicious activity and quarantining devices to minimize botnet spread throughout the network.
Botnets
Botnet activity remained fairly consistent throughout the year except for May, in which activity spiked by 48%. The spike is attributed to the ZeroAccess botnet, which was the top-witnessed botnet during 2020 with close to 1,000,000 sightings.
Total Events
Unique Variants
Total Activity
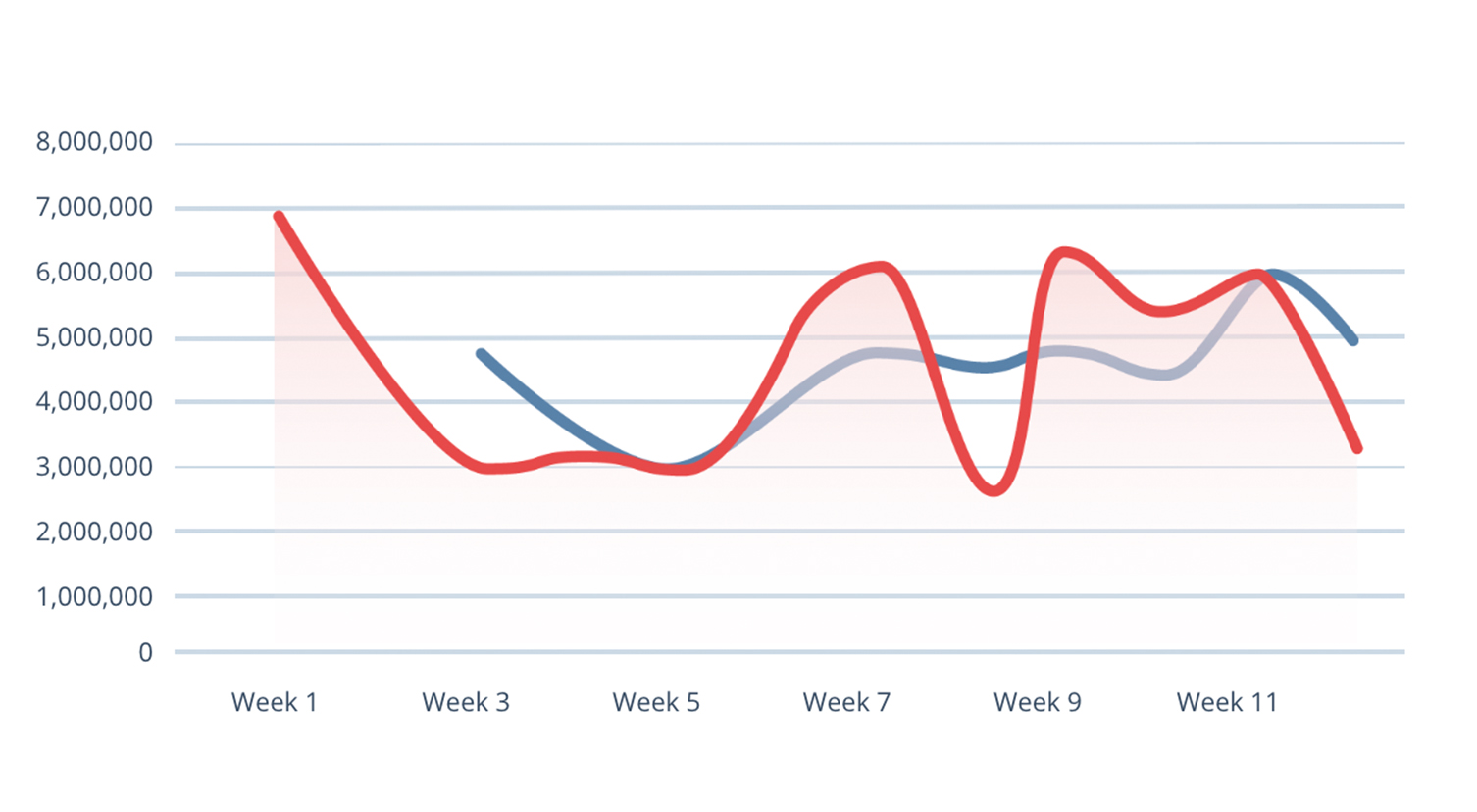
Exploits
Detection, Q4 2020Q4 exploit activity syncs closely with the release of intelligence about 49,000+ Fortinet FortiOS SSL-VPN devices vulnerable to CVE-2018-13379 and with a massive increase of SMB Login brute force attempts.
How to Combat
Stop exploits before they do harm by patching systems and security monitoring to thwart attackers and decrease risk.
Exploits
Exploit activity, which increased 116% for the year, reached its highest volume in December. Attackers searched for new vulnerabilities as well as old, unpatched vulnerabilities with a focus on remote connections. DoublePulsar was the top-utilized technique, followed by SMB Login brute force and HTTP Server Authorization Buffer Overflow.