Interactive Report Summary
Q3 2023 Cyber Threat Report
Top Findings at a Glance

Industry Spotlight: Hospitality Services
Data breaches, ransomware attacks and phishing schemes have become prevalent threats in the hospitality services industry, impacting major chains and smaller establishments. The interconnected nature of services, from third-party booking platforms to in-room IoT devices, has expanded potential vulnerabilities. We’ve seen threat actors launch a variety of attacks, such as spear phishing, brute forcing, OS credential dumping, adversary-in-the-middle attacks and more.
MGM Resorts International recently suffered a crippling cyberattack, causing a substantial $100 million setback in its Q3 results. The breach, attributed to the ALPHV ransomware group in collaboration with Scattered Spider, exploited social engineering tactics, particularly vishing, to impersonate an MGM employee and gain unauthorized access.
This breach exposed customer data, including sensitive information such as SSNs and passport details. The incident, coupled with a similar attack on Caesar's Entertainment, underscores the significant risks posed by neglecting the human aspect of security. While MGM contained the breach, it experienced a 6% drop in its share price and erosion of brand trust.
Methodology
How Nuspire produces its threat intelligence
Hover over tiles to learn more
JULY THROUGH SEPTEMBER
Q3 2023 in Review
Q3 2023 proved busy for Microsoft, which announced patches for 8 zero-days.
Total Events
Unique Variants
Total Activity
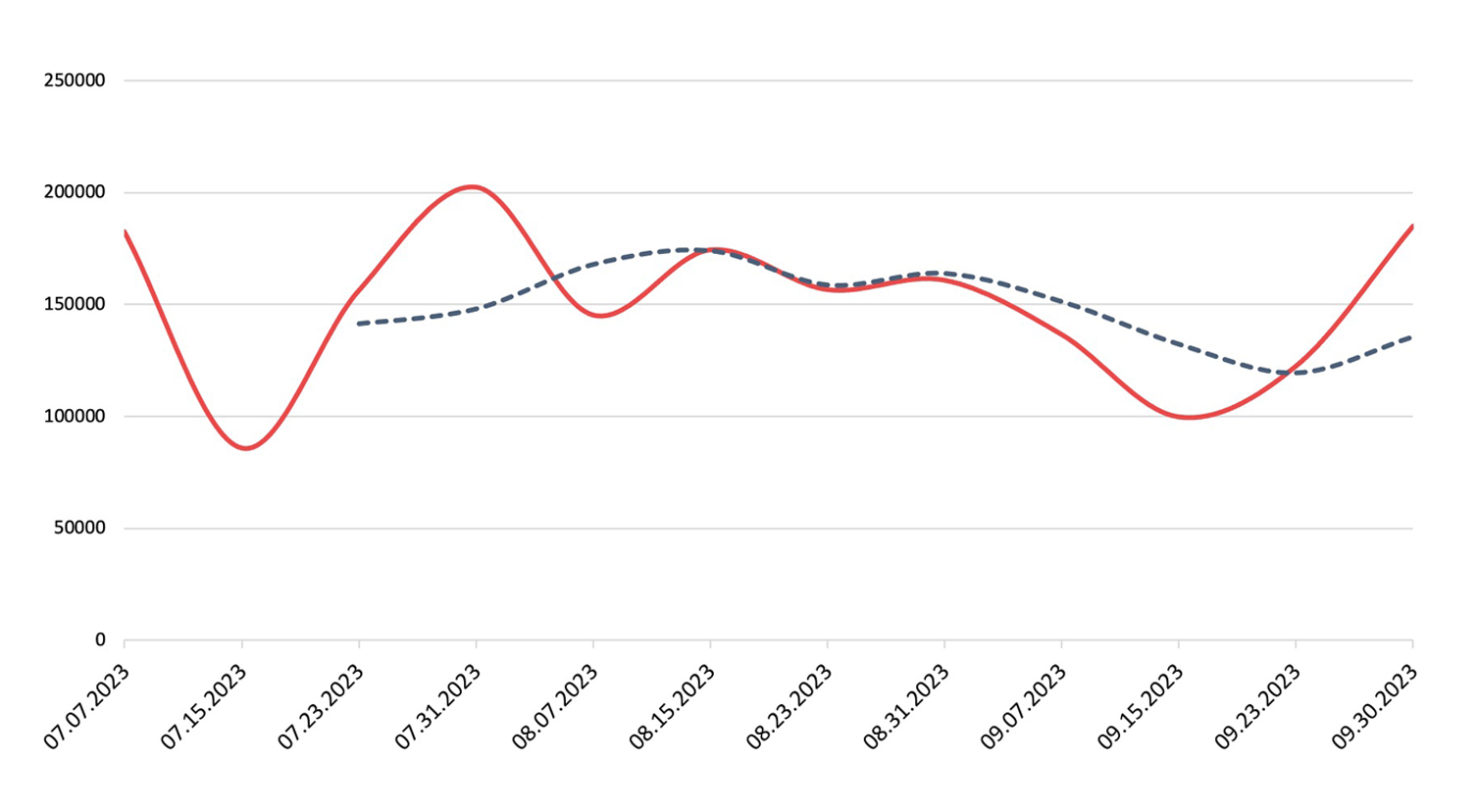
Malware
Detection, Q3 2023Across Nuspire-managed and monitored devices, there was a decrease of 5.94% in total malware activity compared to Q2 2023
How to Combat
To strengthen your defenses against malware activity, you’ll need to adopt a multiprong approach, including endpoint protection platforms and cyber awareness training.
Malware
While we saw a decrease in total malware detections in Q3, ransomware maintained the high level of activity Nuspire witnessed in Q2. In addition, two new contenders joined the list of most active ransomware families for Q3: 8Base and Akira.
Total Events
Unique Variants
Total Activity
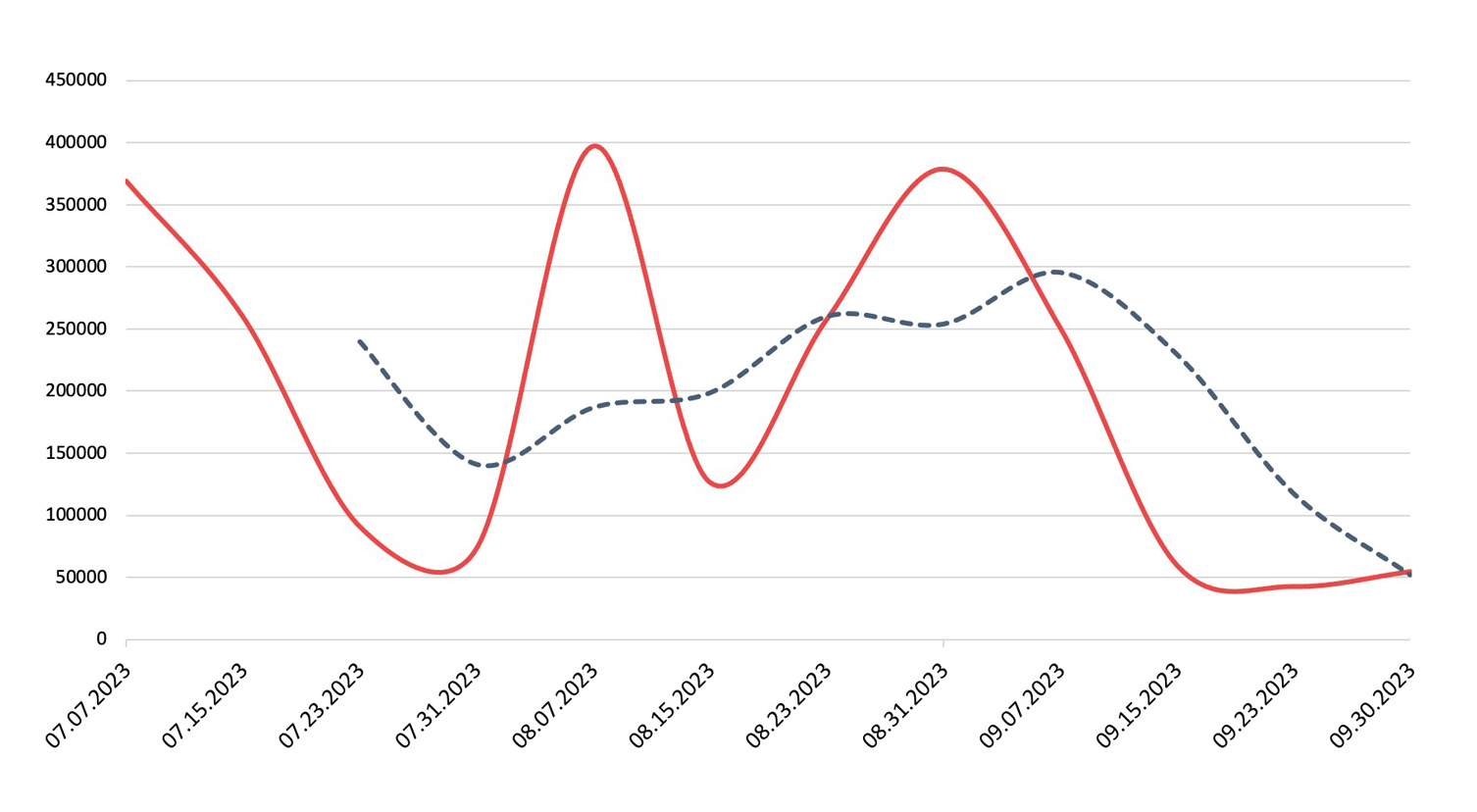
Botnets
Detection, Q3 2023Nuspire saw a staggering 67.51% increase in botnet activity.
How to Combat
Step up your efforts to stop botnet activity, which is usually detected post-infection. We recommend detecting malicious activity and quarantining devices to minimize botnet spread throughout the network.
Botnets
Botnet activity skyrocketed in Q3, with top botnet Torpig Mebroot, clocking an increase in activity of nearly 93% over Q2. An older botnet, TorrentLocker, re-emerged in Q3 as a favorite attack method. The botnet is primarily delivered through phishing emails, enticing victims with unpaid invoices, undelivered packages or unpaid fines.
Total Events
Unique Variants
Total Activity
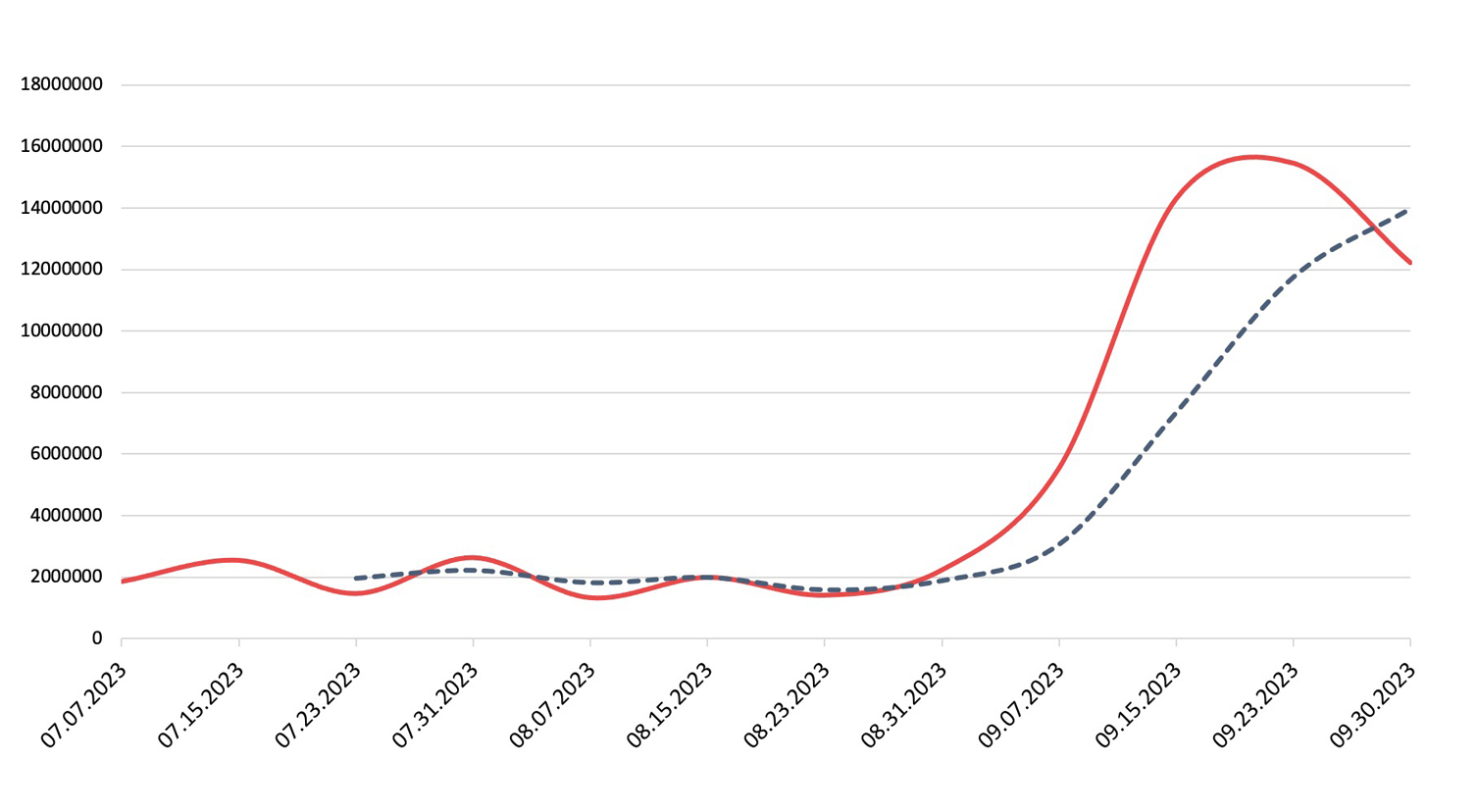
Exploits
Detection, Q3 2023Exploit activity dropped 35.92%
How to Combat
Stop exploits before they do harm by patching systems and security monitoring to thwart attackers and decrease risk.
Exploits
While exploits saw a decrease in activity in Q3, what didn’t change was the astronomical volume of brute forcing attacks aimed at the Secure Shell (SSH) and Server Message Block (SMB) protocols. When examining specific exploits outside of brute forcing (which dwarfs all other exploit activity), we found Apache Log4j remained the most popular. Following closely behind is HTTP Server Authorization Buffer Overflow, a formidable exploit targeting potential flaws in server authorization mechanisms, enabling threat actors to run arbitrary code on affected systems.