Interactive Report Summary
Q2 2021 Threat Report
Top Findings at a Glance
Lesson learned in Q2 2021: Cybersecurity is not a solo effort. Q2 brought some major news in ransomware, including the Colonial Pipeline attack, the disbandment of the DarkSide and REvil ransomware gangs and, as we head into Q3, the arrival of the newest gang to the block, BlackMatter.

If Botnet activity continues to trend up, Q3 may shine a light on major events connected to the increase in detections.
Nuspire witnessed an increase of SSH brute forcing by 34,310.07%.
Methodology
Hover over tiles to learn more
Q2 2021 in Review
April through June
Total Events
Unique Variants
Total Activity
Malware
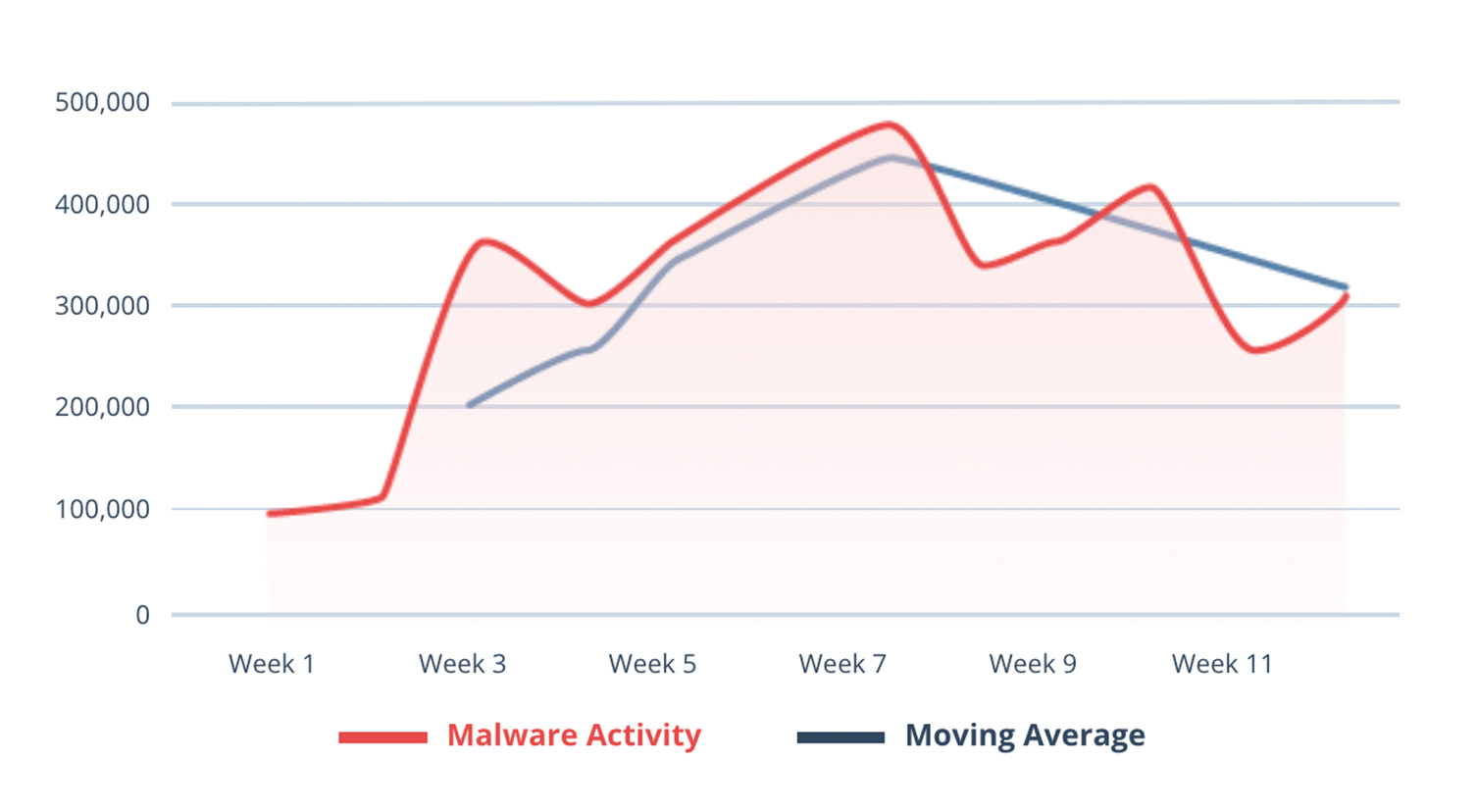
Detection, Q2 2021Across Nuspire managed and monitored devices, there was a 41.84% increase in total malware activity compared to Q1.
How to Combat
To strengthen your defenses against malware activity you’ll need to adopt a multiprong approach including endpoint protection platforms and cyber awareness training.
Malware
VBA agent activity decreased throughout Q1, and as predicted, it’s now back on the rise ― increasing 269.94% from the beginning of the quarter to peak activity in week 10. Activity often comes and goes in waves while threat actors retool, develop new capabilities and adjust phishing lures.
Total Events
Unique Variants
Total Activity
Botnets
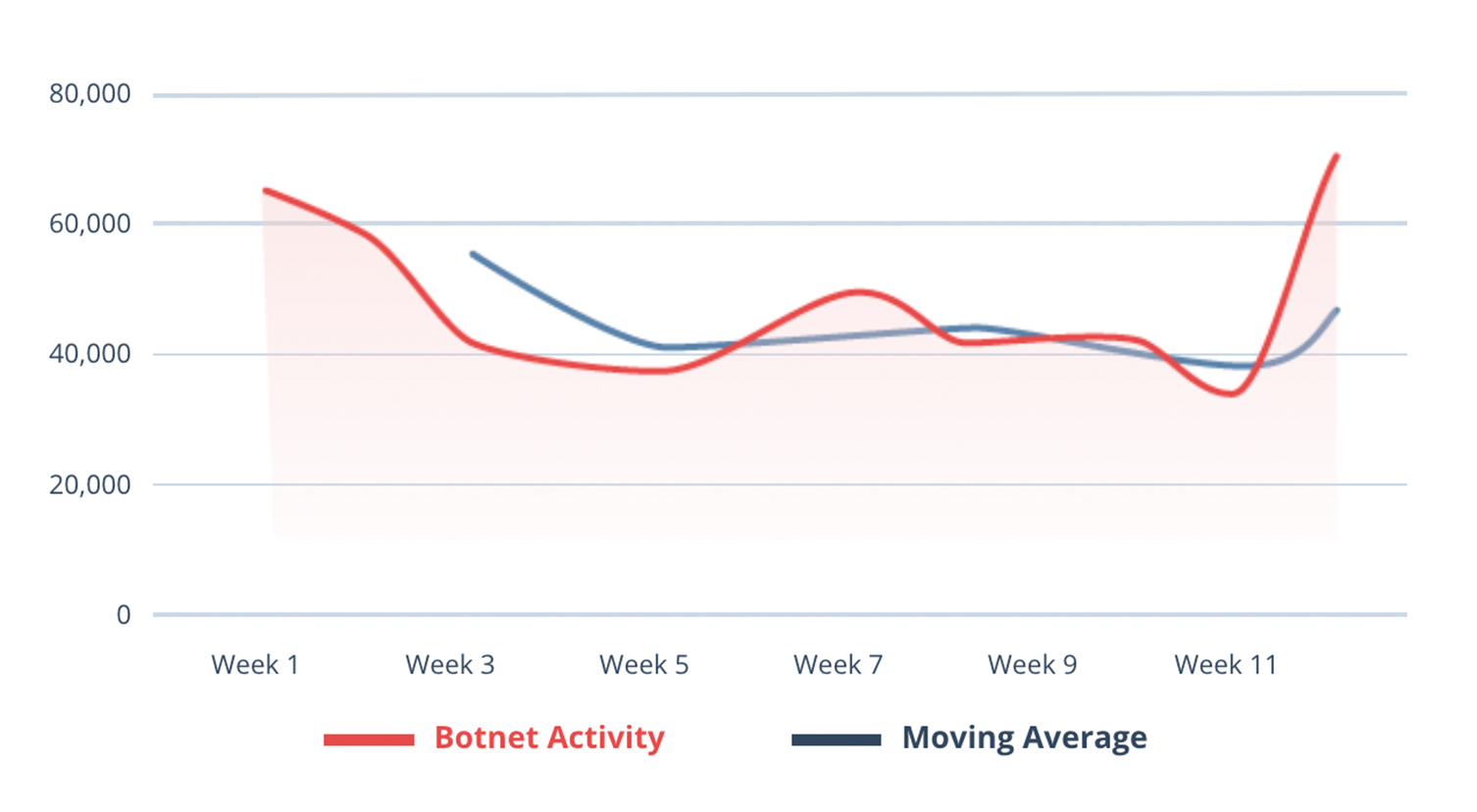
Detection, Q2 2021Overall, there was a 50.34% decrease in botnet activity observed compared to Q1 2021.
How to Combat
Step up your efforts to stop botnet activity, which is usually detected post-infection. We recommend detecting malicious activity and quarantining devices to minimize botnet spread throughout the network.
Botnets
The decrease in activity likely can be attributed to the Q1 shutdown of the Emotet botnet, which significantly impacted the botnet space. Generally, activity observed during Q2 was provided by the Andromeda and Torpig botnets, which typically have been the most active since Emotet’s disruption.
Total Events
Unique Variants
Total Activity
Exploits
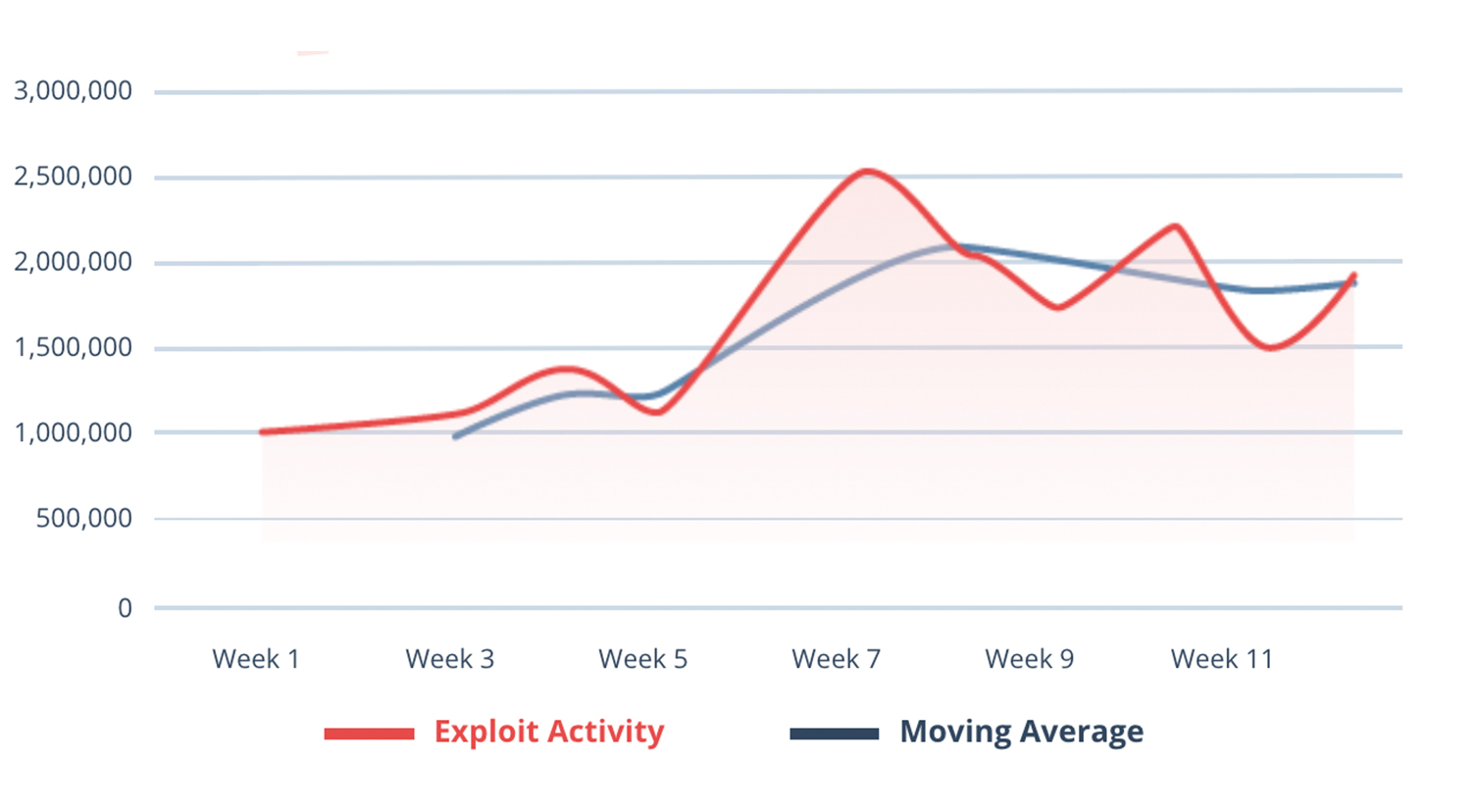
Detection, Q2 2021Throughout Q2, Nuspire witnessed an increase in brute force attacks focused on SMB and SSH logins. SMB attacks continually increased throughout the quarter with a total increase of 8,458.92%.
How to Combat
Stop exploits before they do harm by patching systems and security monitoring to thwart attackers and decrease risk.
Exploits
SSH login brute force attempts also shared a similar story with the exception of activity beginning to trail off after week 8. From the beginning of the quarter to the peak of activity, Nuspire witnessed an increase of SSH brute forcing by 34,310.07%.