What healthcare organizations need to know about HIPAA and cybersecurity
As emerging threats target the health care industry it’s important for these organizations to maintain Health Insurance Portability and Accountability Act (HIPAA) compliance. For a health care provider to remain compliant with the guidelines and requirements established by HIPAA, patients’ sensitive information must be safeguarded.
HIPAA compliance is complex. We can help with that!
What is HIPAA and how does it relate to cybersecurity?
HIPAA is the United States legislation that provides data privacy and security provisions for safeguarding medical information. As the threat landscape has evolved targeting more health care providers, the HIPAA law continues to provide an important framework for preventing a security breach.
The part of the act related to cybersecurity is the Security Rule. The Security Rule safeguards Protected Health Information that exists in an electronic form (ePHI). This Security Rule is based on three types of security safeguards: Administrative, Technical, and Physical. Each includes a series of requirements designed to address specific risks associated with the confidentiality, integrity, and availability of ePHI data. ePHI may be stored and processed on a variety of systems including: Electronic Health Record (EHR) systems, desktop computers, smart devices, databases, and imaging systems. A holistic approach to securing PHI is necessary to maintain HIPAA compliance.
Click here to view our Health Check Ebook
Who does this apply to?
This law applies to health care providers, health plans and health care clearinghouses. Health care providers typically include hospitals, health clinics, nursing homes, doctors, dentists, pharmacies, chiropractors, and psychologist while health plans include HMO’s, health insurance providers, company health plans, and well as government programs such as Medicaid, Medicare and veteran’s health programs.
HIPAA Security Rule Requirements
Each safeguard in the HIPAA Security Rule has a specific set of requirements that need to be in place to ensure data security and to identify potential vulnerabilities and risks.
- Administrative Safeguards: These requirements define the policies and operating procedures for how an organization will follow the security rule. Administrative Safeguards relate to process-oriented controls, such as policies, risk analysis, termination procedures, and training.
- Physical Safeguards: This determines how an organization will control physical access to locations where ePHI exists. The focus here is on the physical controls that protect ePHI-containing systems and related facilities and equipment from natural and environmental hazards, as well as unauthorized access.
- Technical Safeguards: These are automated security controls including: access control, audit controls, integrity control and transport security (typically encryption for network traffic). When implemented, these controls grant access to ePHI data through unique user accounts, automatic account logout, and user authentication.
Consequences and fines
When an organization is breached, it not only effects patient confidence in the organization, but failure to comply subjects the provider to serious fines depending on the situation. These fines can range from $100 to $50,000 per violation, with a maximum penalty of $1.5 million per year for each violation.
According to the U.S. Department of Health & Human Services, in 2018, the Office for Civil Rights (OCR) concluded a record in HIPAA enforcement activity that totaled $28.7 million in fines.
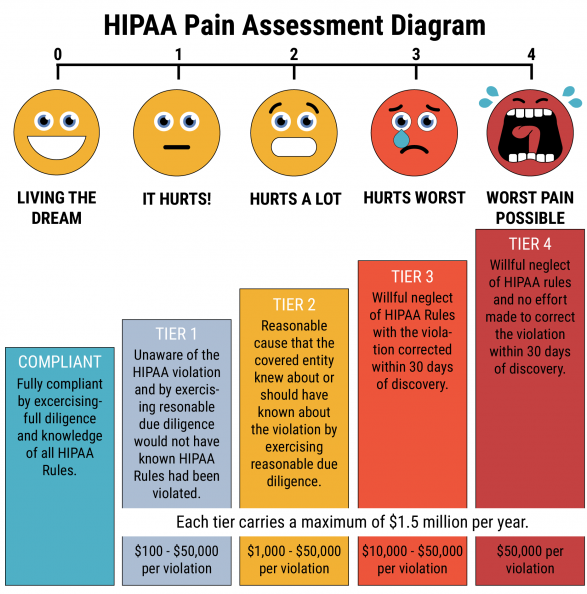
Being compliant is crucial for all health care organizations. However, being compliant is only the start to truly safeguarding patient data. Since the law is not customizable, organizations may check the boxes for compliance, yet fall short of a strong security posture that can effectively protect from cyber threats. Organizations need to make sure that they have a security program customized to best fit their needs while also ensuring their technologies and networks are being monitored 24x7x365 to prevent, detect, contain and remediate threats that enter the network.
For more information on what you can do to ensure your health care organization is compliant and safe from today’s cyber threats, contact Nuspire today and request a free consultation.

